Strategic Lawsuits Against Public Participation (SLAPP)
SLAPP stands for "Strategic Lawsuit Against Public Participation." It refers to a lawsuit filed in retaliation for speaking out on a public issue or controversy. You might be "SLAPPed" for actions such as posting a blog entry, posting a comment on another person's blog, writing a letter to the editor of a newspaper, testifying before the legislature, reporting official misconduct, or circulating a petition. Often, SLAPPs are brought by corporations, developers, or government officials against individuals or community organizations that oppose their actions.
Lawsuits targeting individuals who post anonymously on the Internet, usually because their posted messages criticize the actions of public figures or corporations, are sometimes called cyberSLAPPs. Like a regular SLAPP, a cyberSLAPP aims at chilling free speech by intimidating critics with the prospect of defending an expensive lawsuit. But it also often aims at uncovering the identity of the anonymous critic. For more information on the court procedures a lawyer or party can use to identify an anonymous Internet speaker, see Potential Legal Challenges to Anonymity.
Most SLAPPs ultimately would fail if litigated fully, but the SLAPP filer doesn't usually intend to do so. As previously mentioned, the point of a SLAPP is to intimidate and silence the target through the threat of an expensive lawsuit. Although the First Amendment to the U.S. Constitution protects freedom of speech, the U.S. legal system generally gives the benefit of the doubt to a party bringing a lawsuit until the fact-finding stage, and a winning defendant is not usually entitled to recover attorneys' fees to cover the expense of legal defense (as in some other countries). This means that, even if the claim ultimately fails, the process of defending against a SLAPP through the legal system can be a daunting and expensive prospect for many individuals.
To guard against the chilling effect of SLAPPs, twenty-eight states, the District of Columbia, and one U.S. territory have enacted anti-SLAPP statutes. The U.S. jurisdictions with anti-SLAPP statutes are: Arizona; Arkansas; California; Delaware; District of Columbia; Florida; Guam; Georgia; Hawaii; Illinois; Indiana; Louisiana; Maine; Maryland; Massachusetts; Minnesota; Missouri; Nebraska; Nevada; New Mexico; New York; Oklahoma; Oregon; Pennsylvania; Rhode Island; Tennessee; Texas; Utah; Vermont; and Washington.
Two other states, Colorado and West Virginia, do not have anti-SLAPP statutes, but their courts have recognized a defense to lawsuits that target activities aimed at petitioning the government for action on issues of public importance. These common law (i.e., judge-made) rules offer similar protections to those provided by some anti-SLAPP statutes.
If you get sued in a state with an anti-SLAPP law, you may be able to dismiss the lawsuit at an early stage of the proceeding and recover your costs and attorneys' fees. If you live in a state with an anti-SLAPP law but someone sues you in a state without one, you may be able to argue that the laws of your state should apply. For example, if you are a journalist in California (which has an anti-SLAPP statute) writing about the local community impact of the actions of a corporation based in Iowa (which does not have an anti-SLAPP law), you may be able to argue that California law should apply even if the corporation files a lawsuit in Iowa.
See the state pages for state-specific information on anti-SLAPP laws.
Types of SLAPPs
SLAPP suits come in many forms. Some of the common claims asserted in SLAPPs include:
Defamation: Defamation is the term for a legal claim involving injury to reputation caused by false statements of fact and includes both libel (typically written or recorded statements) and slander (typically spoken statements). Defamation is the most common basis for a SLAPP suit. An individual or organization might file a defamation lawsuit in reaction to criticism or negative commentary published on- or offline, such as in a blog post, news report, letter to the editor, or speech at a public meeting, just to name a few. For more information, see the Defamation section.
Interference with contract or economic advantage: This claim alleges that you intentionally interfered with a contract or other business relationship between the plaintiff and a third party that would have benefited the plaintiff economically. You also might see this claim referred to as "tortious interference with business relations," "tortious interference with contract," or some like-sounding phrase. In the publishing context, you often see this claim included along with a defamation claim. Like a defamation claim, individuals and organizations tend to bring this claim in response to criticism or negative commentary published on- or offline, or political activity that hampers the plaintiff's activities.
Intentional infliction of emotional distress: This claim alleges that the defendant intentionally or recklessly committed some outrageous act that caused the plaintiff extreme emotional distress. As above, in the publishing context, you often see this claim included along with a defamation claim, and it often comes in response to criticism or negative commentary published on- or offline.
Conspiracy: A conspiracy is an agreement between two or more persons to commit an illegal act. A plaintiff might claim that you and someone else conspired to commit defamation, to interfere with a contract, or to intentionally inflict emotional distress. Often, the plaintiff will not even identify who you allegedly have conspired with, naming instead an unspecified number of "John Does" or "Jane Roes" in the complaint.
Keep in mind that, at least at the outset, calling a lawsuit a SLAPP is a subjective evaluation of the merit of its legal and factual claims. If someone sues you, the complaint will not identify itself as a SLAPP, and the person filing the lawsuit will vigorously deny characterization of it as a SLAPP. In the end, you cannot definitively establish that a lawsuit is a SLAPP until a court has ruled on the question.
How To Protect Yourself Against a SLAPP
Be aware that when you are speaking out on a matter of public controversy that involves significant private interests or the reputation of a government official, you may find yourself the target of a SLAPP. By being prepared, you can minimize your risk of being SLAPPed and continue to exercise your rights with confidence.
Know your rights
Under the Constitution, you have a right to free speech and to petition the government. Courts have interpreted these rights to form legal doctrines that protect the types of activities that attract SLAPPs. Note, however, that the Constitution generally does not protect defamatory, threatening, or harassing speech.
Tell the truth
Truth is an absolute defense to a defamation claim. You can protect yourself by not publishing rumors or scandalous innuendo, and you may want to avoid broad, sweeping generalizations or speculative rhetoric in favor of accurate, fact-based statements.
Diligent fact-checking will make you a harder target for a SLAPP suit. Always cite to legitimate sources. Public records are an excellent source of solid factual information. For more information on how to use the law to obtain government records, see Access to Government Information. If you use Internet sources, print out the website page in case the information there changes at a later date.
Even if what you publish ultimately turns out not to be true, you could still have a defense if the subject of your publication is a public figure, such as a celebrity, a government official, or someone who takes on an important role in the relevant debate or controversy. Public figures must prove that you made false statements about them with "actual malice" -- that is, you actually knew that your statements were false or recklessly disregarded their falsity.
In a defamation lawsuit, a court will not hold you liable for stating an opinion. But, be aware that simply adding the words "in my opinion" to the beginning of a sentence will not necessarily help you. For example, if you write, "In my opinion, Mayor Jones is taking bribes from local developers," you could be liable for defamation, unless the statement is true. In addition, if your opinion implies the existence of facts that can be proven true or false, then it is a statement of fact and not opinion for legal purposes, and you could be held liable for publishing it if the underlying facts turn out to be false.
For more information on how to protect yourself against a defamation claim, see the Defamation section.
Insurance
Insurance may be a good way to protect yourself from the expense of defending against a SLAPP. Your homeowners or renters insurance may cover damages and legal fees if someone sues you for defamation, invasion of privacy, or other legal claims. Most homeowners and renters policies, however, exclude coverage for "business pursuits," and a court might find that your online activities are a business pursuit if you earn advertising income from your site or blog or you collect money through other online means. The rules vary from state to state. If your state excludes coverage for business pursuits and you make sufficient money from your site to be excluded, media liability insurance might be a better option, although for many it is prohibitively expensive. See our Finding Insurance section for details on all these insurance-related issues.
What To Do If You Think You've Been SLAPPed
If someone files a lawsuit against you, and you believe it is a SLAPP, you should seek legal assistance immediately. Be aware of the deadline for filing a response to the complaint; if you miss the deadline, the court may enter a judgment against you without hearing your side of the case.
As noted above, twenty-six states and one U.S. territory have enacted anti-SLAPP statutes to help protect citizens who speak out. These anti-SLAPP laws vary in effectiveness, and some have not yet been tested in a legal case. As a general matter, however, they attempt to shift some of the costs and burdens of litigation from you to the person filing the SLAPP suit. See State Law: SLAPPs for state-specific information.
Some common provisions of anti-SLAPP statutes include:
- Protection for speech on issues of public significance and/or activities aimed at petitioning the government for action on economic, social, and political issues;
- Procedural mechanisms for obtaining early dismissal of a SLAPP;
- Recovery of attorneys' fees and court costs incurred in defending against a SLAPP;
- Expedited review of motions to dismiss in order to reduce the time and costs of litigation; and
- Limits or stays on discovery while the court considers a motion to dismiss under the anti-SLAPP law.
If you live in a state with an anti-SLAPP law, you will want to move quickly to get the case dismissed. It is a good idea to seek legal assistance in getting the case dismissed. Keep in mind that, although hiring legal help is expensive, you can recover your attorneys' fees if you win your motion. In addition, there may be public interest organizations that would be willing to take on your case for free or for a reduced rate. The First Amendment Center has an excellent list of organizations that can help. You'll want to find help as soon as you can because successfully filing and arguing a motion to dismiss can be complicated, and you and your lawyer need to move quickly to avoid missing important deadlines.
If your insurance company provides you with a lawyer who is not familiar with SLAPP cases, that lawyer may want to try to settle the case in order to minimize costs. This may sound like a good idea, but a settlement will likely include the condition that you do not discuss the matter in the future. With such a settlement, the SLAPP has been successful, because you cannot publicize the SLAPP filer's abuse of the legal system to chill public debate. Consider arranging to hire an attorney who is knowledgeable about SLAPP law.
In addition to getting the case dismissed, you may want to consider going on the offensive. Eight states have statutes allowing "SLAPPback" suits, which are filed as counterclaims against a SLAPP or in a separate lawsuit. These states are California, Delaware, Hawaii, Minnesota, Nevada, New York, Rhode Island, and Utah. A SLAPPback is a lawsuit you can bring against the person who filed the SLAPP suit to recover compensatory and punitive damages for abuse of the legal process. Even if your state does not have a statute addressing SLAPPbacks, you may be able to sue your opponent for malicious prosecution or abuse of process under the common law of your state. However, you should not underestimate the considerable expense required to bring a SLAPPback, like any lawsuit, to a successful conclusion.
Anti-SLAPP Law in New York
Note: This page covers information specific to New York. For general information concerning Strategic Lawsuits Against Public Participation (SLAPPs), see the overview section of this guide.
New York's anti-SLAPP laws, found at N.Y. Civ. Rights Law §§ 70-a, 76-a and N.Y. C.P.L.R. §§ 3211(g), 3212(h), offer protection against SLAPPs brought by individuals or entities seeking permits or applications from a government body (like zoning permits) over efforts of the defendant to report on, comment on, rule on, challenge, or oppose such application or permission. The statute does not protect "free speech" in the abstract; it only protects bloggers, non-traditional journalists, and other online publishers when they address this narrow class of issues (i.e., the granting or denial of a public permit or application).
Activities Covered By The New York Anti-SLAPP Statute
To use New York's anti-SLAPP law, you must show two things. First, you must show that the plaintiff suing you is a "public applicant or permittee." Second, you must show that the plantiff's claim against you is an "action involving public petition and participation."
The statute defines a "public applicant or permittee" as an individual or entity that has obtained or is seeking "a permit, zoning change, lease, license, certificate or other entitlement for use or permission to act from any government body." The term could include real estate developers, mining companies, garment manufacturers, and private landowners looking to build new structures on their land, among others. In essence, to meet this requirement, you will have to show that the party suing you requires some sort of government license to operate or proceed with a project.
The statute defines an "action involving public petition and participation" as one that involves a public applicant or permittee (above) seeking damages from a defendant on the basis of the defendant's efforts "to report on, comment on, rule on, challenge or oppose" the application to the government. For example, the definition would include a garment manufacturer's lawsuit against a public interest organization campaigning to have the manufacturer's state registration revoked. For another, the definition would include a real estate developer's lawsuit against a blogger who reported on the developer's attempts to secure a building permit, or who called upon local citizens to oppose the application.
How To Use The New York Anti-SLAPP Statute
The New York anti-SLAPP statute gives you the ability to file a motion to dismiss a complaint brought against you by a public applicant or permittee over your efforts to report on, comment on, challenge, or oppose an application to the government.
If you are served with a complaint that you believe to be a SLAPP, you should seek legal assistance immediately. Successfully filing and arguing a motion to dismiss can be complicated, and you and your lawyer need to move quickly to avoid missing important deadlines. Keep in mind that, although hiring legal help is expensive, you may be able to recover your attorneys' fees if you win your motion. In addition, there may be public interest organizations that would be willing to take on your case for free or for a reduced rate. The First Amendment Center is a good place to start.
In ruling on a motion to dismiss under the anti-SLAPP laws, a New York court will determine whether the plaintiff is a "public applicant or permittee" and whether the lawsuit is an "action involving public petition and participation," as described above. If you can establish these two things, then the court will require the plaintiff to demonstrate that its lawsuit "has a substantial basis in law." If the plaintiff fails to do so, then the court will grant your motion and dismiss the case. On the other hand, if the plaintiff's case is strong, then the court will not grant your motion to dismiss, and the lawsuit will move ahead like any ordinary case.
Note that, unlike in many states, New York's anti-SLAPP motion does not halt discovery (i.e., fact gathering for trial). Thus, you may incur additional litigation expenses while the court hears and decides your motion.
What Happens If You Win A Motion To Dismiss
If you prevail on a motion to dismiss under the New York anti-SLAPP law, the court may award you one or more of the following kinds of damages: costs and attorneys' fees, other compensatory damages, and punitive damages. To receive costs and attorneys' fees, you must show that the plaintiff's lawsuit against you lacked a basis in fact and law. To get compensatory damages (i.e., damages that compensate you for any other harm you suffered as a result of the SLAPP), you must also show that the plaintiff was maliciously attempting to impair your right to free speech or petition. Further, if you can show that if that the attempt to impair your rights was the only reason the plaintiff sued you, you may be entitled to punitive damages.
Note that even if you are able to establish that you meet the requirements for any or all of the types of damages listed above, the court does not have to award those damages. All anti-SLAPP damages, including costs and attorneys' fees, are awarded at the court's discretion under New York law.

DNS Changer Malware: how to detect it and protect yourself
Published by Jon Watson - on March 24, 2017
The Domain Name System (DNS) is the part of internet infrastructure that resolves easily-remembered domain names that humans use into more obscure IP addresses that internet-connected computers use. Without DNS, we would have to remember the IP address of every new site we want to visit.
In that regard, DNS seems mostly related to convenience. In reality, DNS is also a critical part of internet security. Your computer trusts DNS to give it the correct IP address for any given site. Sadly, there are very few precautions in place to detect incorrect DNS responses, which leaves a security gap for bad guys to exploit.
Deeper dive into how DNS works
DNS is decentralized. Rather than being comprised of one massive database with information about every domain, that information is scattered around the internet on many different servers. Each domain has at least one authoritative name server.
Background: An
authoritative name serveris a DNS server that contains all the DNS records for any particular domain.
For example, in the case of Comparitech.com, we can see the authoritative name servers are Amazon DNS servers.
$ dig +short comparitech.com ns
ns-769.awsdns-32.net.
ns-1652.awsdns-14.co.uk.
ns-1459.awsdns-54.org.
ns-237.awsdns-29.com.Therefore, if I were to query one of those name servers to get the IP address for the website comparitech.com, it will return the IP address of the web server that the site is hosted on.
$ dig +short comparitech.com @ns-769.awsdns-32.net.
108.59.8.18In that example, I queried one of Comparitech’s name servers directly, but that is not quite how the DNS system works in day-to-day operation. The complete DNS system involves not only DNS servers, but also DNS clients. DNS clients are called DNS resolvers.
Background: A
DNS resolveris named that way because its job is to take a domain name and resolve it to an IP address that your computer can use to initiate communication to the internet server.
A DNS resolver resides on almost every computer and also usually at higher levels such as your internet service provider. When a program on your computer wants to know the IP address of a domain it asks the DNS resolver to resolve that domain-to-IP relationship. How the resolver does that is not known by the requesting program; it is just happy to get an IP address back regardless of how it was obtained.
Almost all DNS resolvers cache queries in order to reduce load on the various DNS servers. The DNS resolver on your computer is called the local resolver and when it queries for an IP address it will first check its cache to see if it already knows that answer. If it does not, it will then refer to the next level DNS resolver, which is usually your router. That resolver does the same cache check to see if knows the answer already and if not, then it refers the request to the next, higher resolver. This continues until a resolver is encountered that has the answer and supplies the IP address, or until the hierarchy is exhausted and no resolvers nor the authoritative name servers know the IP address of the domain. The latter normally only happens when the domain is not registered and therefore has no authoritative name servers, or there is some other malfunction in the DNS resolver chain.
The important part of this process is that once a resolver supplies an answer, the search stops. No other resolvers will be queried as soon as one resolver succeeds. Therein lies the gap in which DNS changer malware can take hold. More on that later.
There is one last layer to DNS resolution which is not part of the DNS model but has great power nonetheless. Each computer has a file named hosts somewhere on its system. In Unix and macOS/OSX systems it is usually found at /etc/hosts/ and for Windows systems it is usually found in C:\System32\drivers\etc\hosts. If you’re running a more exotic operating system the location of its hosts file is probably in this list.
In almost all cases, the hosts file trumps any DNS resolver activity. Meaning, if I put the following line into my hosts file, I will never be able to successfully load the Comparitech.com website. This is because the incorrect answer in my hosts file will be accepted by my web browser and, because no other resolvers are queried once an answer is returned, no more checks will be performed.
123.45.67.89 comparitech.com www.comparitech.comThe hosts file pre-dates DNS and was originally used for ARPANET name resolution, but it still exists in systems today. It’s primary used by technical people such as developers and systems administrators when there is a need to temporarily view a domain on a different IP address than the one stored in the public DNS.
The hosts file can also be modified so as to block the IP addresses of malicious websites. You can learn how to modify your hosts file to block ads and malware here.
Lastly, there are a variety of different types of DNS records. For example, mail servers are designated by MX records, IPv6 addresses are contained in AAAA records, and domain aliases are called CNAME records. For the purposes of this article we’ll just focus on the IPv4 A record, which holds the IPv4 address of the domain and is used primarily as the website IP address.
Where do DNS records come from?
Domain owners are responsible for creating the necessary DNS records for their domain to function. These records need to be created at wherever the authoritative name server is for that domain. When a domain is first purchased from the domain registrar those records normally point to some type of parking page at the registrar. Once a website or other service is created for the domain, normally the DNS records are changed to point to the new website and mail server.
Background: A domain registrar is the place where a domain name is purchased or has been transferred to after purchase. The archaic term
registraris used because an important function of a domain seller is to register that domain in the DNS system so that its DNS records can be resolved.
How does DNS changer malware work?
The object of DNS changer malware is to cause your computer to visit different services than you intend and make doing so entirely invisible to you. For example, a hacker creating a duplicate of the Bank of America website on some other server is only half the battle. The next step is to somehow get people to visit that site and unwittingly enter their login credentials so they can be sent to the bad guys.
This is a form of phishing. One common way to try to trick people into visiting these sites is through spam email campaigns with obfuscated links in them. The links look like they go to the legitimate Bank of America site, but in fact do not. This type of phishing is fairly easily defeated with some basic investigation techniques that I’ve written about here.
A more insidious and difficult-to-detect method is to change your local DNS resolver to provide the malicious IP address to queries for the Bank of America domain. This means that you would launch your web browser and visit the Bank of America website. Your browser would ask the local DNS resolver for the IP address of the BoA site and the corrupted DNS resolver would return the IP address of the malicious site instead of the IP address of the legitimate BoA site. The malicious site would load in your browser and, unlike typical phishing sites that reside on other domains, this site would actually show as the Bank of America in your browser address bar, which makes the misdirection pretty near impossible to detect.
Recall that once a DNS resolver receives an an answer, it accepts that answer and performs no further queries. This means that in order to provide an incorrect IP address for a DNS query, a bad guy just has to intercept the first DNS resolver that is going to handle your DNS requests. In almost all cases, that is the local DNS resolver on your own computer or your router. The attack vector is to install malware on your own computer that takes control of your local or router DNS.
History of DNS Changer malware
The first round of DNS changer malware appeared in 2013 and has been soundly defeated. It was a complicated affair set up by a company in Estonia named Rove Digital. It operated a series of malicious DNS servers that injected ads into web pages. Rove then deployed Windows and Mac OSX malware far and wide that reconfigured local resolvers to use those malicious DNS servers. More than $14 million worth of ads were clicked on before they were shut down.
Because of the nature of that attack, the malicious DNS servers were discovered and catalogued. It was therefore pretty easy to remediate; it simply amounted to checking the DNS settings on your computer and comparing them to a list of known Rove DNS servers. If there was a match, you were infected. A consortium named the DNS Change Working Group (DCWG) was set up to help users diagnose and remedy their infections. Most of the links on that site are now dead.
While not technically malware, China has been known to poison its own DNS as a censorship tool. The DNS servers Chinese citizens use are configured to return incorrect IP addresses for sites that the Cyberspace Administration of China department wants to render unavailable inside the country.
See also: How to access sites blocked in China with a VPN.
In the past these DNS servers would return null IPs which did not host any content so that the visitor’s browser would just time out. In a more recent twist, China’s DNS appears to be responding with the IP addresses of legitimate sites that it does not approve of elsewhere in the world which has resulted in some of those sites going down due to the amount of traffic they suddenly receive from unwitting Chinese visitors.
Background: The phrase “poison DNS” means to deliberately modify a DNS server to return incorrect IP addresses for a domain or set of domains. DNS changer malware essentially modifies your local network use poisoned DNS servers.
Current state of DNS changer malware
Current iterations of the DNS Changer malware are much more sophisticated and much harder to detect. While injecting ads to make money is still a principal goal of the DNS changer malware, it is more insidious and also redirects people to malicious sites in order to commit various types of fraud. One major difference is that it now targets routers instead of individual computers. Targeting routers is a much more efficient attack vector because it allows a single router infection to poison the DNS of all the devices using that router. In a typical home or office setting, a single router provides DNS to a very large number of devices without the bother of trying to infect each individual device’s local DNS resolver.
Anatomy of a modern DNS Changer malware attack
The DNS Changer malware of today is deployed via javascript during a typical drive-by attack.
Background: A
drive-byattack is the unintended download of javascript to your browser from an infected website that you visited. The term is a tongue-in-cheek reference to the indiscriminate way in which drive-by shootings claim arbitrary victims.
Once the javascript is downloaded, it executes a WebRTC call to determine your IP address. If your IP address matches a predetermined set of rules, then an advertisement containing hidden router fingerprints and default router administrator login credentials is downloaded to your computer. That information is then extracted to determine what type of router you have. It then tries to log in to your router with the default credentials for your brand of router in order to change your DNS settings. Proofpoint discovered how this process works and has a blow-by-blow description of how each step takes place here.
How to detect if you’ve been infected
Without the well-defined attack vector that Rove Digital used, it’s much harder to detect if you’ve been infected. However, there may be some clues that indicate a problem.
SSL errors or no SSL at all
SSL (more correctly called TLS these days) stands for Secure Sockets Layer (TLS stands for Transport Layer Security and has superseded SSL). SSL has two main jobs:
- encrypt information between your browser and the web server, and
- confirm the identify of the web server.
The second point is performed when the certificate is purchased. The certificate vendor has an obligation to ensure that the person requesting a certificate for a domain is the actual owner of that domain. This prevents just any person from obtaining a Bank of America SSL certificate, for example. There are differing levels of validation required before a certificate can be issued:
- Domain Control Validation: The least level of validation which only requires the certificate vendor to ensure that the requester has physical control of the domain.
- Organization Validation: Unlike domain validation that is only concerned with proving control of the domain, organizational validation further seeks to prove that the organization requesting the certificate is a valid, legal organization. To confirm this, some investigation into the organization is performed.
- Extended Validation: This is the highest level of validation and organizations seeking to obtain EV certificates must prove their business is legitimate and properly licensed in their jurisdiction.
Although mistakes do happen, it is theoretically impossible to obtain a certificate if you can’t prove you own the domain. So, even if a bad guy were able to corrupt your DNS, you would end up at a website that has either no SSL at all, or broken SSL that your browser would warn you about. If you notice a site that used to have SSL no longer does, or if you see browser warnings about SSL problems on a site, you may not be on the site where you think you are. (Read more: The Complete Beginner’s Guide to SSL Encryption)
Increase in ads or redirection to pages containing ads
Malware developers make money off of ads. A few cents per click ads up to a lot when you can make millions of people click on them. If you notice an increase in ads, or if you’re being redirected to pages containing ads, that is almost certainly a sign of malware, and possibly DNS changer malware.
Check your router’s DNS settings
Almost every router on the market today has a settings page where DNS servers can be defined. In most cases, DNS servers are dictated by your Internet Service Provider (ISP) and the DNS settings in your router will be empty. But it’s possible to override your ISP’s DNS servers by setting specific DNS servers in your router, which is exactly what the DNS Changer malware seeks to do. There are two steps to determine if your router has been infected:
- Check the DNS settings in your router. If they’re not empty, then:
- Determine if the DNS servers listed are malicious.
Each router is different, so it’s not possible to list instructions on how to find the DNS settings for every router. You’ll need to look for a DNS Servers setting. In some cases it is in the WAN (Wide Area Network) settings:
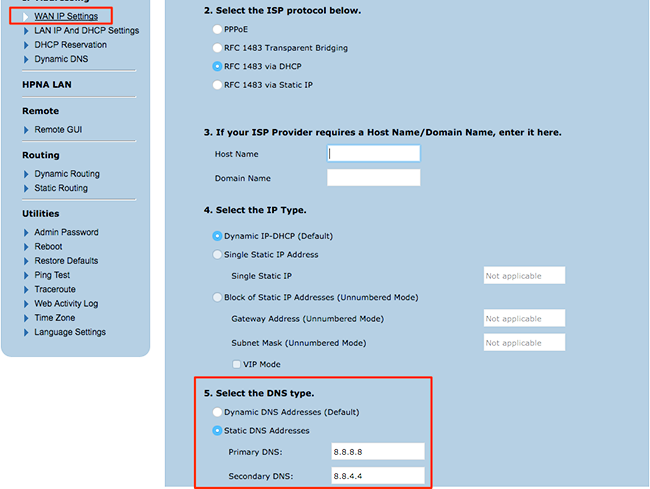
In other cases you may find it in the Local Network settings:
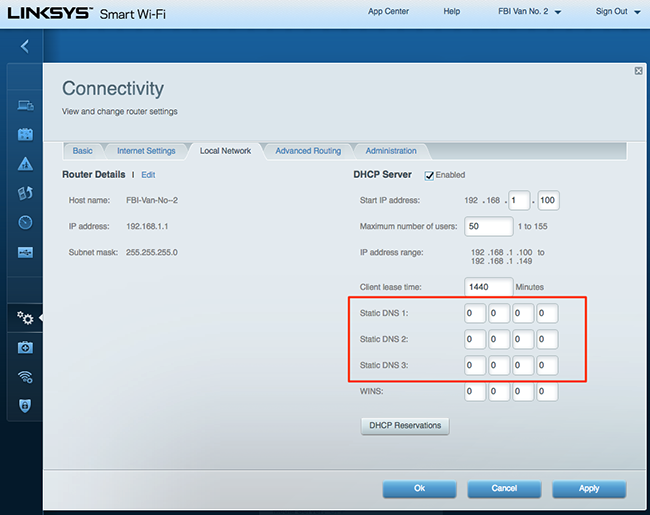
You may need to consult your router documentation to find the proper place to view your router’s DNS settings.
Using my two-step test above on the first screenshot I can determine that:
- My router’s DNS settings are NOT empty so I proceed to step 2.
- I recognize 8.8.8.8 and 8.8.4.4 as Google’s DNS servers, so I know they are not malicious.
But if I was not sure, I would Google those IPs to see who they belong to:
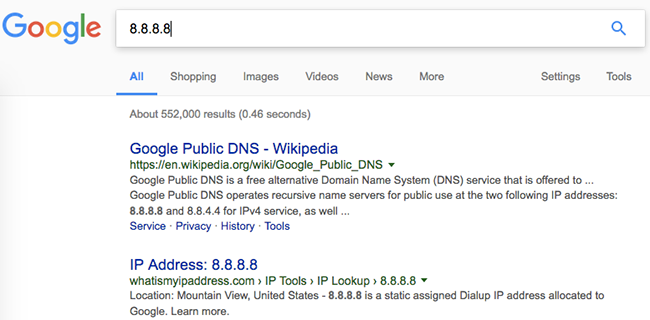
If you find entries in your router’s DNS settings and you’re unable to determine where they come from, you should remove them.
Check your local computer DNS settings
While today’s version of the DNS Changer malware primarily attacks routers, it can’t hurt to verify your individual computer’s DNS settings.
macOS
Apple -> System Preferences -> Network -> click on your network
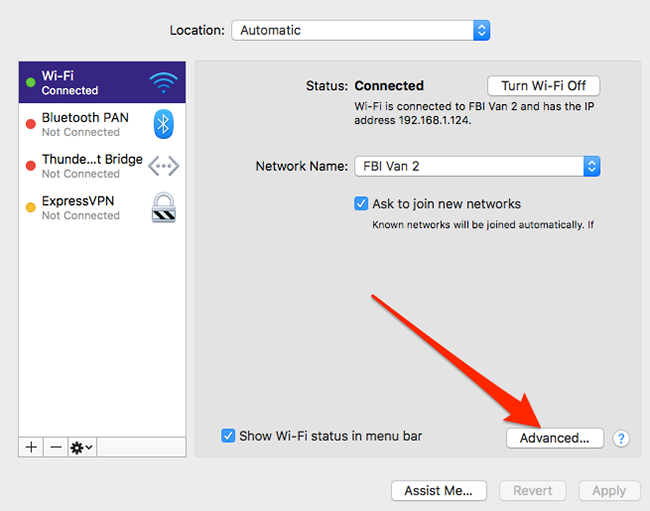
Windows
Control Panel -> Network and Internet -> Network Connections -> right click your network connection and select Properties
Internet Protocol Version 4 (TCP/IPv4)Internet Protocol Version 6 (TCP/IPv6)
Click properties:
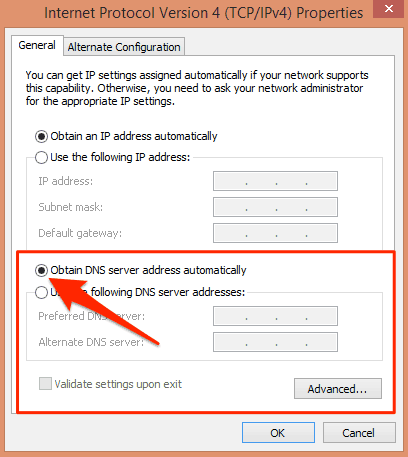
Click Advanced if you want to add more DNS servers.
Check current settings from command line:
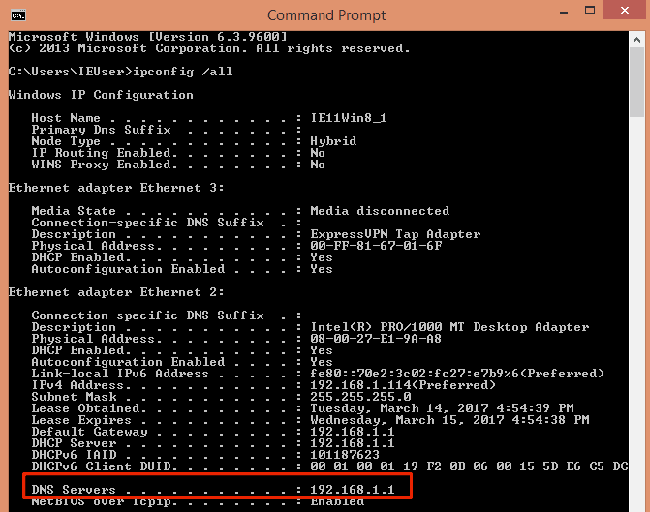
How to protect yourself against infection or reinfection
Recall that modern DNS Changer malware attempts to identify your router and then use the default login credentials against it. Therefore, the first and best protection against this is to simply change your router’s admin password as soon as you can. That simple action alone will foil this particular strain of malware.
It’s also important to note that the attack uses javascript and webRTC to succeed. I’ve written about the dangers of surfing with javascript enabled and also how to disable webRTC queries. There’s a vocal minority that feel the web completely breaks if your surf with javascript disabled, but as a multi-year veteran of doing just that I can assure you the web is just fine. Even if it was not, the old adage applies: convenience or security – pick one
. There’s also no reason to allow webRTC queries at all for most of us. If you’re curious about whether you’re allowing webRTC queries you can use this DNS Leak Test and install a plugin for Chrome or Firefox to disable it.
If you’ve already been infected and have found malicious DNS servers in your router or in your local DNS settings, then you likely have malware on your system. We maintain a list of the best antivirus solutions, and you should run one of them to scan your system for this type of malware.
It’s important to do things in the right order. If you’ve found malicious DNS entries in your router or local computer, removed them, and then installed antivirus software, you will want to re-visit your DNS settings after the malware scan is complete. The reason for this is that the malware that changed your DNS settings likely still existed on your system until the malware scan was complete. Those bad DNS entries in your router that you removed could have been immediately replaced by the extant malware. Only after you’ve run an antivirus scan and removed that malware can you be more confident that your DNS settings will stay as you intended.
Different Faces - Same Cults - Fighting An Unknown Enemy Not Possible - Know Thy Enemy
- By Bahram Maskanian - February 19, 2017
Are you one of the parasite ruling class? In search of more power, money and control? No problem, false flag operation works every time, first create a horrendous bloody problem, scare the public to death, then offer the unthinkable solution, which would deliberately cause more problems, each designed to include further abolishing of peoples’ liberty and erosion of U.S. Constitution, plus openly embezzling billions in funding. Never solve any of the problems, to keep the never ending fear and funding flowing. We, the American people understand, we have already became expert in this sort of problem, reaction, solution racket.
False flag operations and fear mongering is the oldest highly effective hoax in tyrant’s tool chest. That is how tyranny and tyrants operate. For so long the whole world has been misled to believe there is so called “deep state, or shadowy government, or invisible enemy”, plus the hoopla and secrecy associated with deep state, spreading highly misleading and bogus information, deceiving those in search of answers, to go around a never ending circle.
People live their lives based on their perception. The brainwashing effect of Entertainment, Television and Hollywood (Human Sees, Human Told, Human Does) is one of the powerful tools used by the parasite ruling class. We, the people must become fully aware of the said fact and stay vigilant at all times.
The parasite ruling class consists of psychopath, zionist, eugenist, racist, warmongering, mass murdering aristocratic families, bankers and the European monarchs. Starting from Cecil Rhodes using his vast stolen fortunes from plundering South Africa; down to Lord Milner, Lord Selborne, Sir Patrick Duncan, Field Marshal Jan Smuts, Lord Lothian, Lord Brand, Meyer Amschel Rothschild; together orchestrated and funded secret organizations with the goal of eradicating 90% of humanity. To murder millions of innocent children, women and men, to gain tight control over planet Earth and rule the world. Handed down the eugenist baton to Rockefeller, Rothschild, Morgan, Carnegie, Schiff, Harriman and Warburg crime families to continue behind the scenes. Also there are the low level parasites such as, but not limited to: George Soros, Bill Gates, Mike Bloomberg and alike.
Through establishment of the Royal Institute For International Affairs (Secret Round Table) the parasite ruling class penetrated governments, press, media, finance, civil societies and universities all over the world and gain total control from within. But since in the United States, American people did not care about royalties, it was named The Council on Foreign Relations (CFR) - Must Read “The Anglo-American Establishment - Secret Society” and “Tragedy and Hope” written by professor Carroll Quigley, 1949.
The “obvious psychopath state” has been behind 119 horrible wars, some of which lasted over 100 years, colonial wars of aggression to conquer Africa, Australia, New Zealand, North and South America are just a few of the said wars since year 1400, up to 2012. Making billions in financing wars, followed by confiscating mineral rich continents and territories. Plundering, enslaving the young and murdering the rest of innocent native people. The parasite ruling class fabricated the usury central banking system, communism, fascism and virtually every evil befallen upon humanity is caused by the obvious psychopath state, or the parasite ruling class ever-since.
We must not fall for the false flags, tricks and traps along the way. We must be alert and aware at all times. The enemy will not give-up without a fight. There are millions of us, and hundreds of the ruling parasites. We must inform and educate our fellow police officers and U.S. Armed forces personnel. Our fight has to be nonviolent, revealing, all-inclusive, none-reactive, intelligent, enlightening and decisive. Our best and most powerful weapon is noncompliance, simply must disobey the ruling parasites illegal and unconstitutional decrees and mandates.
The first and the most important task to neutralize the parasite ruling class is to reform the current highly corrupt predetermined election system. Once each State in the union has instituted a trusted paper ballot election system in place, we, the people can begin electing ethical and compassionate folks, thus together begin rebuilding and repairing all of our, economical, social and political ills.
Great Book Regarding Tragedy and Hope Written By Joe Plummer - https://www.joeplummer.com/
Tragedy and Hope - And The Anglo-American Establishment - Secret Society


