
DNS Changer Malware: how to detect it and protect yourself
Published by Jon Watson - on March 24, 2017
The Domain Name System (DNS) is the part of internet infrastructure that resolves easily-remembered domain names that humans use into more obscure IP addresses that internet-connected computers use. Without DNS, we would have to remember the IP address of every new site we want to visit.
In that regard, DNS seems mostly related to convenience. In reality, DNS is also a critical part of internet security. Your computer trusts DNS to give it the correct IP address for any given site. Sadly, there are very few precautions in place to detect incorrect DNS responses, which leaves a security gap for bad guys to exploit.
Deeper dive into how DNS works
DNS is decentralized. Rather than being comprised of one massive database with information about every domain, that information is scattered around the internet on many different servers. Each domain has at least one authoritative name server.
Background: An
authoritative name serveris a DNS server that contains all the DNS records for any particular domain.
For example, in the case of Comparitech.com, we can see the authoritative name servers are Amazon DNS servers.
$ dig +short comparitech.com ns
ns-769.awsdns-32.net.
ns-1652.awsdns-14.co.uk.
ns-1459.awsdns-54.org.
ns-237.awsdns-29.com.Therefore, if I were to query one of those name servers to get the IP address for the website comparitech.com, it will return the IP address of the web server that the site is hosted on.
$ dig +short comparitech.com @ns-769.awsdns-32.net.
108.59.8.18In that example, I queried one of Comparitech’s name servers directly, but that is not quite how the DNS system works in day-to-day operation. The complete DNS system involves not only DNS servers, but also DNS clients. DNS clients are called DNS resolvers.
Background: A
DNS resolveris named that way because its job is to take a domain name and resolve it to an IP address that your computer can use to initiate communication to the internet server.
A DNS resolver resides on almost every computer and also usually at higher levels such as your internet service provider. When a program on your computer wants to know the IP address of a domain it asks the DNS resolver to resolve that domain-to-IP relationship. How the resolver does that is not known by the requesting program; it is just happy to get an IP address back regardless of how it was obtained.
Almost all DNS resolvers cache queries in order to reduce load on the various DNS servers. The DNS resolver on your computer is called the local resolver and when it queries for an IP address it will first check its cache to see if it already knows that answer. If it does not, it will then refer to the next level DNS resolver, which is usually your router. That resolver does the same cache check to see if knows the answer already and if not, then it refers the request to the next, higher resolver. This continues until a resolver is encountered that has the answer and supplies the IP address, or until the hierarchy is exhausted and no resolvers nor the authoritative name servers know the IP address of the domain. The latter normally only happens when the domain is not registered and therefore has no authoritative name servers, or there is some other malfunction in the DNS resolver chain.
The important part of this process is that once a resolver supplies an answer, the search stops. No other resolvers will be queried as soon as one resolver succeeds. Therein lies the gap in which DNS changer malware can take hold. More on that later.
There is one last layer to DNS resolution which is not part of the DNS model but has great power nonetheless. Each computer has a file named hosts somewhere on its system. In Unix and macOS/OSX systems it is usually found at /etc/hosts/ and for Windows systems it is usually found in C:\System32\drivers\etc\hosts. If you’re running a more exotic operating system the location of its hosts file is probably in this list.
In almost all cases, the hosts file trumps any DNS resolver activity. Meaning, if I put the following line into my hosts file, I will never be able to successfully load the Comparitech.com website. This is because the incorrect answer in my hosts file will be accepted by my web browser and, because no other resolvers are queried once an answer is returned, no more checks will be performed.
123.45.67.89 comparitech.com www.comparitech.comThe hosts file pre-dates DNS and was originally used for ARPANET name resolution, but it still exists in systems today. It’s primary used by technical people such as developers and systems administrators when there is a need to temporarily view a domain on a different IP address than the one stored in the public DNS.
The hosts file can also be modified so as to block the IP addresses of malicious websites. You can learn how to modify your hosts file to block ads and malware here.
Lastly, there are a variety of different types of DNS records. For example, mail servers are designated by MX records, IPv6 addresses are contained in AAAA records, and domain aliases are called CNAME records. For the purposes of this article we’ll just focus on the IPv4 A record, which holds the IPv4 address of the domain and is used primarily as the website IP address.
Where do DNS records come from?
Domain owners are responsible for creating the necessary DNS records for their domain to function. These records need to be created at wherever the authoritative name server is for that domain. When a domain is first purchased from the domain registrar those records normally point to some type of parking page at the registrar. Once a website or other service is created for the domain, normally the DNS records are changed to point to the new website and mail server.
Background: A domain registrar is the place where a domain name is purchased or has been transferred to after purchase. The archaic term
registraris used because an important function of a domain seller is to register that domain in the DNS system so that its DNS records can be resolved.
How does DNS changer malware work?
The object of DNS changer malware is to cause your computer to visit different services than you intend and make doing so entirely invisible to you. For example, a hacker creating a duplicate of the Bank of America website on some other server is only half the battle. The next step is to somehow get people to visit that site and unwittingly enter their login credentials so they can be sent to the bad guys.
This is a form of phishing. One common way to try to trick people into visiting these sites is through spam email campaigns with obfuscated links in them. The links look like they go to the legitimate Bank of America site, but in fact do not. This type of phishing is fairly easily defeated with some basic investigation techniques that I’ve written about here.
A more insidious and difficult-to-detect method is to change your local DNS resolver to provide the malicious IP address to queries for the Bank of America domain. This means that you would launch your web browser and visit the Bank of America website. Your browser would ask the local DNS resolver for the IP address of the BoA site and the corrupted DNS resolver would return the IP address of the malicious site instead of the IP address of the legitimate BoA site. The malicious site would load in your browser and, unlike typical phishing sites that reside on other domains, this site would actually show as the Bank of America in your browser address bar, which makes the misdirection pretty near impossible to detect.
Recall that once a DNS resolver receives an an answer, it accepts that answer and performs no further queries. This means that in order to provide an incorrect IP address for a DNS query, a bad guy just has to intercept the first DNS resolver that is going to handle your DNS requests. In almost all cases, that is the local DNS resolver on your own computer or your router. The attack vector is to install malware on your own computer that takes control of your local or router DNS.
History of DNS Changer malware
The first round of DNS changer malware appeared in 2013 and has been soundly defeated. It was a complicated affair set up by a company in Estonia named Rove Digital. It operated a series of malicious DNS servers that injected ads into web pages. Rove then deployed Windows and Mac OSX malware far and wide that reconfigured local resolvers to use those malicious DNS servers. More than $14 million worth of ads were clicked on before they were shut down.
Because of the nature of that attack, the malicious DNS servers were discovered and catalogued. It was therefore pretty easy to remediate; it simply amounted to checking the DNS settings on your computer and comparing them to a list of known Rove DNS servers. If there was a match, you were infected. A consortium named the DNS Change Working Group (DCWG) was set up to help users diagnose and remedy their infections. Most of the links on that site are now dead.
While not technically malware, China has been known to poison its own DNS as a censorship tool. The DNS servers Chinese citizens use are configured to return incorrect IP addresses for sites that the Cyberspace Administration of China department wants to render unavailable inside the country.
See also: How to access sites blocked in China with a VPN.
In the past these DNS servers would return null IPs which did not host any content so that the visitor’s browser would just time out. In a more recent twist, China’s DNS appears to be responding with the IP addresses of legitimate sites that it does not approve of elsewhere in the world which has resulted in some of those sites going down due to the amount of traffic they suddenly receive from unwitting Chinese visitors.
Background: The phrase “poison DNS” means to deliberately modify a DNS server to return incorrect IP addresses for a domain or set of domains. DNS changer malware essentially modifies your local network use poisoned DNS servers.
Current state of DNS changer malware
Current iterations of the DNS Changer malware are much more sophisticated and much harder to detect. While injecting ads to make money is still a principal goal of the DNS changer malware, it is more insidious and also redirects people to malicious sites in order to commit various types of fraud. One major difference is that it now targets routers instead of individual computers. Targeting routers is a much more efficient attack vector because it allows a single router infection to poison the DNS of all the devices using that router. In a typical home or office setting, a single router provides DNS to a very large number of devices without the bother of trying to infect each individual device’s local DNS resolver.
Anatomy of a modern DNS Changer malware attack
The DNS Changer malware of today is deployed via javascript during a typical drive-by attack.
Background: A
drive-byattack is the unintended download of javascript to your browser from an infected website that you visited. The term is a tongue-in-cheek reference to the indiscriminate way in which drive-by shootings claim arbitrary victims.
Once the javascript is downloaded, it executes a WebRTC call to determine your IP address. If your IP address matches a predetermined set of rules, then an advertisement containing hidden router fingerprints and default router administrator login credentials is downloaded to your computer. That information is then extracted to determine what type of router you have. It then tries to log in to your router with the default credentials for your brand of router in order to change your DNS settings. Proofpoint discovered how this process works and has a blow-by-blow description of how each step takes place here.
How to detect if you’ve been infected
Without the well-defined attack vector that Rove Digital used, it’s much harder to detect if you’ve been infected. However, there may be some clues that indicate a problem.
SSL errors or no SSL at all
SSL (more correctly called TLS these days) stands for Secure Sockets Layer (TLS stands for Transport Layer Security and has superseded SSL). SSL has two main jobs:
- encrypt information between your browser and the web server, and
- confirm the identify of the web server.
The second point is performed when the certificate is purchased. The certificate vendor has an obligation to ensure that the person requesting a certificate for a domain is the actual owner of that domain. This prevents just any person from obtaining a Bank of America SSL certificate, for example. There are differing levels of validation required before a certificate can be issued:
- Domain Control Validation: The least level of validation which only requires the certificate vendor to ensure that the requester has physical control of the domain.
- Organization Validation: Unlike domain validation that is only concerned with proving control of the domain, organizational validation further seeks to prove that the organization requesting the certificate is a valid, legal organization. To confirm this, some investigation into the organization is performed.
- Extended Validation: This is the highest level of validation and organizations seeking to obtain EV certificates must prove their business is legitimate and properly licensed in their jurisdiction.
Although mistakes do happen, it is theoretically impossible to obtain a certificate if you can’t prove you own the domain. So, even if a bad guy were able to corrupt your DNS, you would end up at a website that has either no SSL at all, or broken SSL that your browser would warn you about. If you notice a site that used to have SSL no longer does, or if you see browser warnings about SSL problems on a site, you may not be on the site where you think you are. (Read more: The Complete Beginner’s Guide to SSL Encryption)
Increase in ads or redirection to pages containing ads
Malware developers make money off of ads. A few cents per click ads up to a lot when you can make millions of people click on them. If you notice an increase in ads, or if you’re being redirected to pages containing ads, that is almost certainly a sign of malware, and possibly DNS changer malware.
Check your router’s DNS settings
Almost every router on the market today has a settings page where DNS servers can be defined. In most cases, DNS servers are dictated by your Internet Service Provider (ISP) and the DNS settings in your router will be empty. But it’s possible to override your ISP’s DNS servers by setting specific DNS servers in your router, which is exactly what the DNS Changer malware seeks to do. There are two steps to determine if your router has been infected:
- Check the DNS settings in your router. If they’re not empty, then:
- Determine if the DNS servers listed are malicious.
Each router is different, so it’s not possible to list instructions on how to find the DNS settings for every router. You’ll need to look for a DNS Servers setting. In some cases it is in the WAN (Wide Area Network) settings:
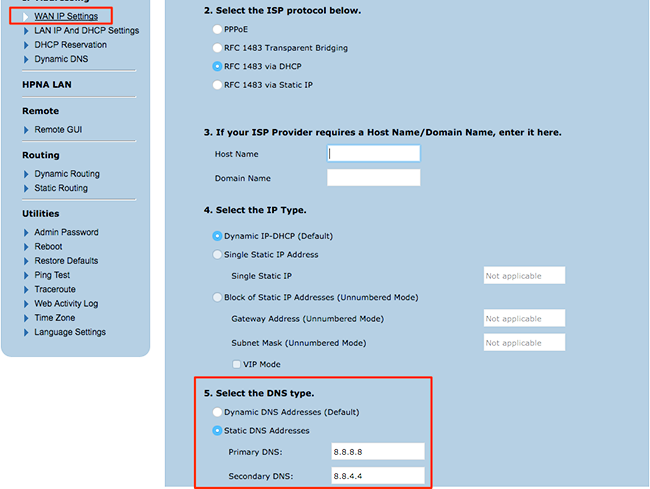
In other cases you may find it in the Local Network settings:
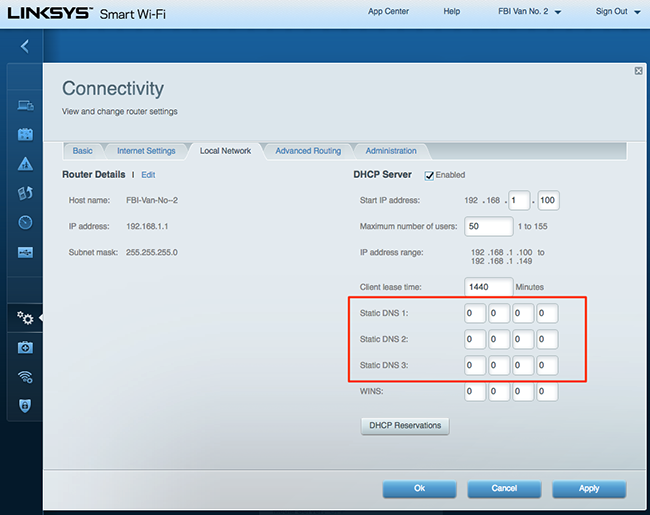
You may need to consult your router documentation to find the proper place to view your router’s DNS settings.
Using my two-step test above on the first screenshot I can determine that:
- My router’s DNS settings are NOT empty so I proceed to step 2.
- I recognize 8.8.8.8 and 8.8.4.4 as Google’s DNS servers, so I know they are not malicious.
But if I was not sure, I would Google those IPs to see who they belong to:
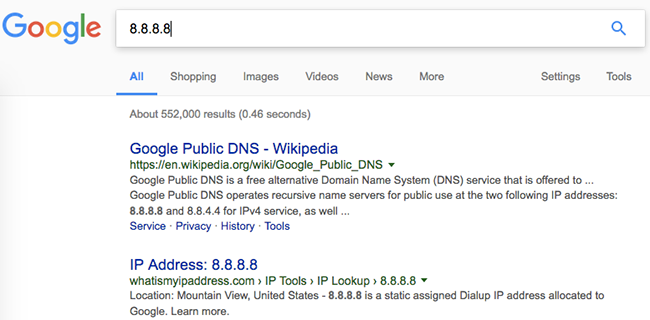
If you find entries in your router’s DNS settings and you’re unable to determine where they come from, you should remove them.
Check your local computer DNS settings
While today’s version of the DNS Changer malware primarily attacks routers, it can’t hurt to verify your individual computer’s DNS settings.
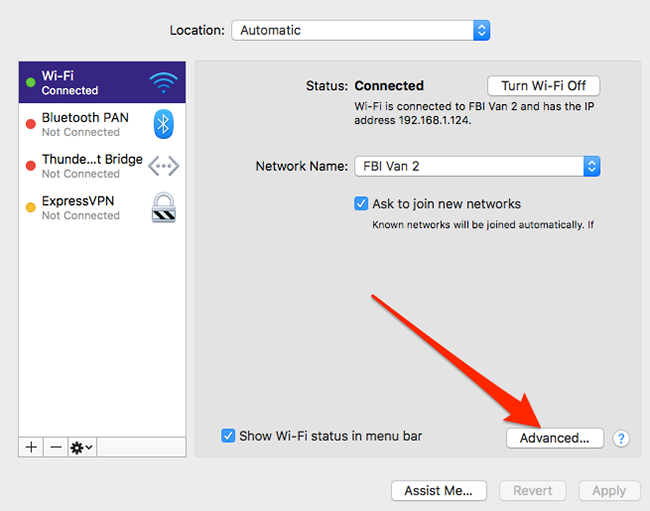
macOS
Apple -> System Preferences -> Network -> click on your network
Windows
Control Panel -> Network and Internet -> Network Connections -> right click your network connection and select Properties
Internet Protocol Version 4 (TCP/IPv4)Internet Protocol Version 6 (TCP/IPv6)
Click properties:
Click Advanced if you want to add more DNS servers.
Check current settings from command line:
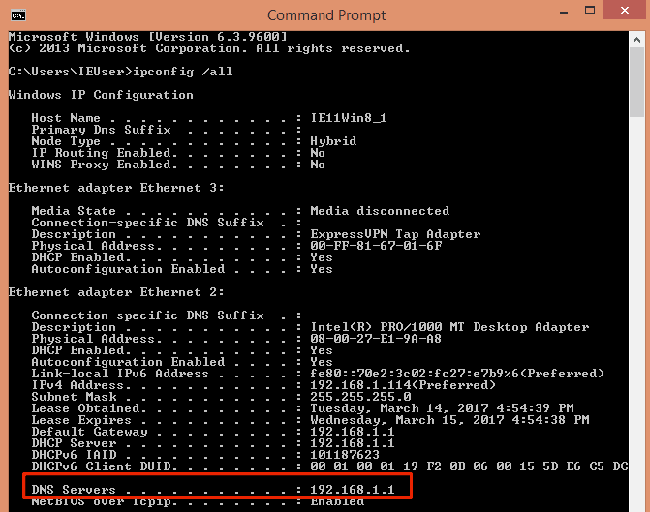
How to protect yourself against infection or reinfection
Recall that modern DNS Changer malware attempts to identify your router and then use the default login credentials against it. Therefore, the first and best protection against this is to simply change your router’s admin password as soon as you can. That simple action alone will foil this particular strain of malware.
It’s also important to note that the attack uses javascript and webRTC to succeed. I’ve written about the dangers of surfing with javascript enabled and also how to disable webRTC queries. There’s a vocal minority that feel the web completely breaks if your surf with javascript disabled, but as a multi-year veteran of doing just that I can assure you the web is just fine. Even if it was not, the old adage applies: convenience or security – pick one
. There’s also no reason to allow webRTC queries at all for most of us. If you’re curious about whether you’re allowing webRTC queries you can use this DNS Leak Test and install a plugin for Chrome or Firefox to disable it.
If you’ve already been infected and have found malicious DNS servers in your router or in your local DNS settings, then you likely have malware on your system. We maintain a list of the best antivirus solutions, and you should run one of them to scan your system for this type of malware.
It’s important to do things in the right order. If you’ve found malicious DNS entries in your router or local computer, removed them, and then installed antivirus software, you will want to re-visit your DNS settings after the malware scan is complete. The reason for this is that the malware that changed your DNS settings likely still existed on your system until the malware scan was complete. Those bad DNS entries in your router that you removed could have been immediately replaced by the extant malware. Only after you’ve run an antivirus scan and removed that malware can you be more confident that your DNS settings will stay as you intended.


